
Leading Bitcoin ATM maker General Bytes disclosed that hackers stole cryptocurrency from the company and its customers using a zero-day vulnerability in its BATM management platform.
General Bytes makes Bitcoin ATMs allowing people to purchase or sell over 40 cryptocurrencies. Customers can deploy their ATMs using standalone management servers or General Bytes cloud service.
Over the weekend, the company disclosed that hackers exploited a zero-day vulnerability tracked as BATM-4780 to remotely uploaded a Java application via ATM's master service interface and run it with 'batm' user privileges.
"The attacker scanned the Digital Ocean cloud hosting IP address space and identified running CAS services on ports 7741, including the General Bytes Cloud service and other GB ATM operators running their servers on Digital Ocean (our recommended cloud hosting provider)," General Bytes explained in a security incident disclosure.
The company took to Twitter to urge customers to "take immediate action" and install the latest updates to protect their servers and funds from attackers.
After uploading the Java application, the threat actors gained able to perform the following actions on compromised devices:
-
Ability to access the database.
-
Ability to read and decrypt API keys used to access funds in hot wallets and exchanges.
-
Send funds from hot wallets.
-
Download user names, their password hashes and turn off 2FA.
-
Ability to access terminal event logs and scan for any instance where customers scanned private keys at the ATM. Older versions of ATM software were logging this information.
General Bytes warned that its customers and its own cloud service were breached during the attacks.
"GENERAL BYTES Cloud service was breached as well as other operator's standalone servers," highlights the statement.
Although the company disclosed how much money the attacker stole, they provided a list of cryptocurrency addresses used by the hacker during the attack.
These addresses show that the hacker began stealing cryptocurrency from Bitcoin ATM servers on March 17th, with the attacker's Bitcoin address receiving 56.28570959 BTC, worth approximately $1,589,000, and 21.79436191 Ethereum, worth roughly $39,000.
While the Bitcoin wallet still contains the stolen cryptocurrency, the threat actors appear to have used Uniswap to convert the stolen Ethereum into USDT.
Upgrade servers now
CAS (Crypto Application Server) admins are urged to examine their "master.log" and "admin.log" log files for any suspicious gaps in time caused by the attacker deleting log entries to conceal their actions on the device.
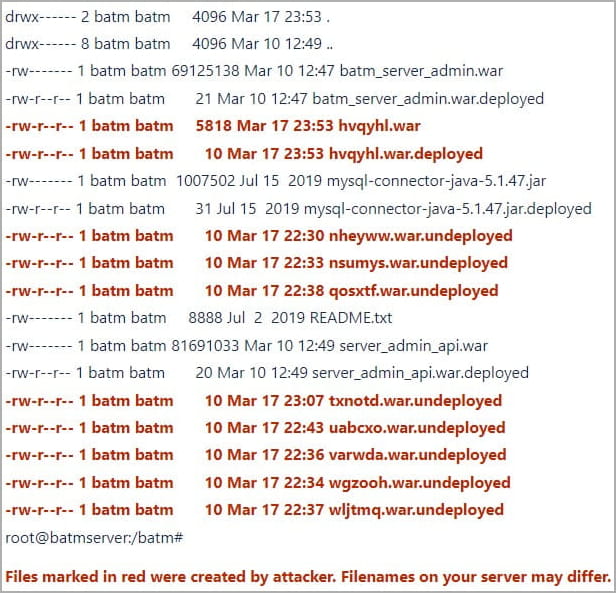
General Byte's report also warned that the uploaded malicious JAVA applications would appear in the "/batm/app/admin/standalone/deployments/" folder as random-named .war and .war.deployed files, as shown below.
The company notes that the file names are likely different per victim.
Those without signs of a breach should still consider all their CAS passwords and API keys compromised and immediately invalidate them and generate new ones. All user passwords should also be reset.
Detailed step-by-step instructions for all server operators on protecting their endpoints are enclosed in the company's statement.
Shuttering the cloud service
General Bytes says they are shuttering its cloud service, stating it finds it "theoretically (and practically) impossible" to secure it from bad actors when it must simultaneously provide access to multiple operators.
The company will provide support with data migration to those who would like to install their own standalone CAS, which should now be placed behind a firewall and VPN.
General Byte has also released a CAS security fix that addresses the exploited vulnerability, provided in two patches, 20221118.48 and 20230120.44.
It also highlights that the breached system underwent multiple security audits since 2021, but none identified the exploited vulnerability.
Furthermore, researchers from the Kraken cryptocurrency exchange found multiple vulnerabilities in General Bytes' ATMs in 2021, which the company quickly fixed
However, even with these security audits, in August 2022, General Bytes had a security incident where hackers exploited a zero-day vulnerability in its ATM servers to steal cryptocurrency from its customers.
The company says its plans to conduct numerous security audits of its products by multiple companies in a short period to discover and fix other potential flaws before bad actors find them.

.jpg)
Comments
Fofabot - 1 year ago
I am trying to search it in fofa.info. Looks like they still have cloud service assets.
FOFA Query: title="Crypto Application Server" || cert="GENERAL BYTES" && banner="Set-Cookie: JSESSIONID="
https://en.fofa.info/result?qbase64=dGl0bGU9IkNyeXB0byBBcHBsaWNhdGlvbiBTZXJ2ZXIiIHx8IGNlcnQ9IkdFTkVSQUwgQllURVMiICYmIGJhbm5lcj0iU2V0LUNvb2tpZTogSlNFU1NJT05JRD0i